《分享》XG與Juniper SRX做IPsec串接 《分享》XG與Juniper SRX做IPsec串接 |       |
順子沒碰過Juniper SRX,但業務帶回來的案子中,有不少需求是與客戶既有的SRX進行串接。
既然這需求備增,那順子也來筆記一下XG如何跟Juniper SRX做IPsec串接。
Juniper上的IPsec VPN有分為route base與policy base兩種,
而Sophos XG為policy base IPsec VPN,所以SRX上的設定自然要以policy base的方式來進行。
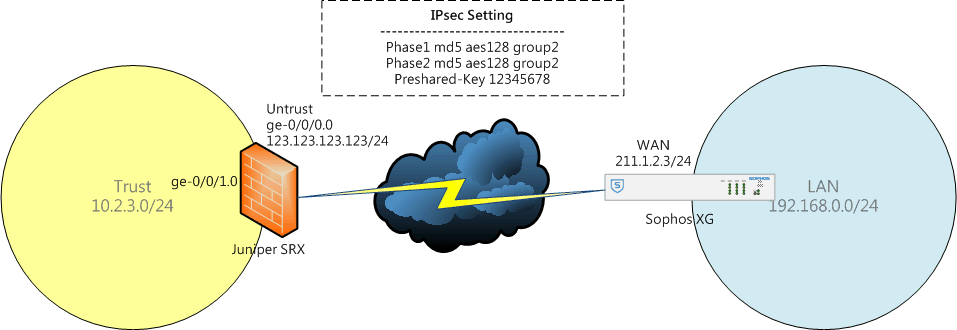
SRX與XG兩端的情境配置如下圖。
參考資料
How to troubleshoot a VPN that is up, bu...passing traffic
Configuring a Policy-Based VPN
password-decrypt.com/

♥順子老婆的網拍,請多關照∼
If you don't like something, change it.
If you can't change it, change your attitude.
Don't complain!
|